To ensure secure configuration and adequately assigning administrative and sensitive access rights in SAP systems is an extremely complex endeavor, which requires experience and very specific knowhow. No wonder that many organizations are struggling with this challenge. How the task to verify the security posture of your SAP environment can become a piece of cake, we will demonstrate in this blog post.
4 reasons to establish an effective SAP Vulnerability Management
But first, let’s begin with the basic question. Why should you even care to ensure an effective Vulnerability Management for your SAP systems?
- Shifting ERP workloads into the cloud leads to vulnerabilities with business-critical applications
In the last few years the attitude of organizations around the world regarding the question to move business-critical workloads into the cloud, significantly changed. In the first couple of years, the market leaders awaited the experiences of “first-mover” companies to go with this new service model. However, in the meantime the direction changed drastically and the journey to the cloud skyrocketed rapidly. Of course, the business-critical SAP application landscape is also affected of this trend. In the migration projects that we support, we often observe that the system landscape is migrated in a “1:1-approach”, which entails serious risks since viable security best practices applicable for cloud environments are not sufficiently adopted. There could potentially exist default users and passwords, which might be exploited by malicious actors. The risk of an exploit of such a vulnerability could increase dramatically due to the fact, that even more holes need to be punched into the network security mechanisms in cloud infrastructures, compared to on-premise architectures.
- The trend of attacks on core systems constantly increased in the past years
Since 2016, the Department of Homeland Security Cyber and Infrastructure Security Agency (CISA) published 5 US-CERT alerts for business-critical applications. An exploit of such a vulnerability can lead to a theft of sensitive data or even a total breakdown of core processes[1]. Even in organizations which are well aware of the risks coming along with such vulnerabilities, the setup of an effective SAP vulnerability management poses a big challenge. The reason lies in the fact that the time from the discovery of a vulnerability until the first scanning activities by malicious actors are observed, is often very short. A functioning exploit is often available after 3 days already. Many companies do not dispose of the processes, the required personnel or the tools to react on vulnerabilities in such an increased pace.
- Existing defense-in-depth strategies do not sufficiently protect core applications
Since the beginning of the cloud journey, it has become obvious that the traditional “fortress principle”, with which core applications are secured by the strongest possible security mechanisms, do not sufficiently protect core applications. However, this approach should not be buried completely, since security holes in the “outer” security perimeter could lead to an open gateway for attackers. This allows attackers to enter the network, moving laterally in the network looking for the “crown jewels”. To identify vulnerabilities in the IT infrastructure, many organizations rely on vulnerability scanning solutions. These are capable of identifying and assessing risks of insecure configurations or software vulnerabilities and to recommend mitigating actions for a wide range of IT components. Typically, these solutions are very strong for infrastructure components. However, they are often quite poor when it comes to identifying vulnerabilities like weak configurations, overly assigned access rights or missing security practices in business applications.
- Even the best security teams are confronted with an increasing workload with unchanged resources
The requirements in regard to securing core applications is increasing due to the aforementioned reasons. The financial resources for security experts in the area of SAP are however very rare. Each month dozens of security weaknesses with different criticality levels and for several system components are published. This makes the task of an effective vulnerability management extremely complex; especially in case the security department operates not only one, but many SAP systems. This might lead to a situation where patches are not appropriately assessed and applied according to their criticality levels. Furthermore, critical access rights are assigned in urgency scenarios due to the fact that there is no time to develop adequate access roles. Organizations should be aware that an exploit of a vulnerability in a core application with viable data can have far-reaching consequences.
Get the security of your SAP systems under control with our SAP Application Security Managed Service
Now you hopefully better understand why establishing a vulnerability management program for SAP systems is of inevitable importance. Nevertheless, the professional implementation of such procedures is not an easy task.
We therefore developed a solution, that allows you to get a cost-efficient overview over the security posture of your SAP systems on the ABAP stack and you can benefit from the following results:
- Overview on the implementation of the security relevant system configurations
- You will get insights on the users able to access your SAP system(s), their critical access rights and will be able to assess if these access rights are appropriate
- You will be able to identify risks in your SAP environment
- You receive meaningful dashboards to present to your management
Unique insights into your SAP security in 5 easy steps
Within a few hours, you receive a qualified statement regarding the assignment of sensitive access rights and the implementation of the SAP system’s security controls. Such an assignment is realized along the following five steps:
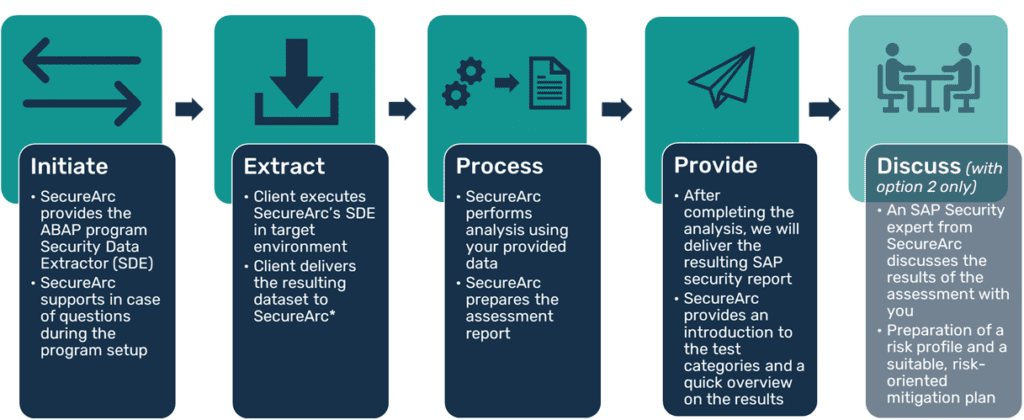
After an initial run, our service can be converted to a simple SAP Security Reporting Service (option 1), which poses an even smaller investment and allows you to achieve a continuous security monitoring for your SAP environment.
SAP security made easy
The previously extremely complex task regarding the identification and assessment of the security posture in your central ERP environment is becoming a breeze with our SAP Application Security Managed Service. SecureArc is able to support you in assessing a significant risk factor in your IT environment and powerfully presenting these risks to your management by applying a high degree of automation.
Are you interested? In this case, do not hesitate to contact us. We are very happy to prepare a proposal shaped to your individual needs.
[1] https://us-cert.cisa.gov/ics/alerts
